Impossible de connecter mon server CalDAV à mon iPhone iOS 14.3
Résolu
guillaumegilbertsoucy
Messages postés
369
Statut
Membre
-
guillaumegilbertsoucy Messages postés 369 Statut Membre -
guillaumegilbertsoucy Messages postés 369 Statut Membre -
Bonsoir,
J'ai déployé mon serveur CalDAV avec Radicale mais je ne suis pas capable de me connecter avec mon iPhone tournant sous iOS 14.3 . Pas de problèmes avec Mozilla Thunderbird.

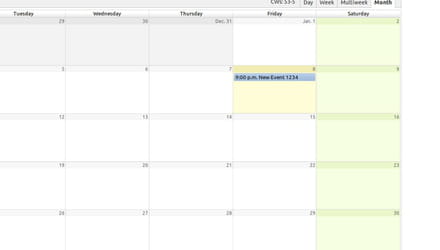
La seule façon dont j'ai été capable de connecter mon serveur CalDAV à mon iPhone c'est en sélectionnant Souscrire:
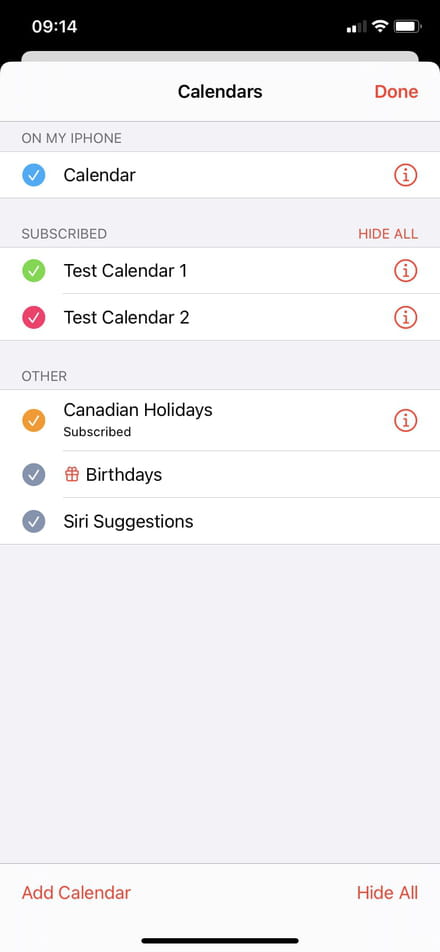
Comment faire pour connecter mon iPhone a mon serveur CalDAV ?
Voici mon fichier de configuration /etc/radicale/config :
# -- mode: conf --
# vim:ft=cfg
# Config file for Radicale - A simple calendar server
#
# Place it into /etc/radicale/config (global)
# or ~/.config/radicale/config (user)
#
# The current values are the default ones
[server]
# CalDAV server hostnames separated by a comma
# IPv4 syntax: address:port
# IPv6 syntax: [address]:port
# For example: 0.0.0.0:9999, [::]:9999
hosts = 192.168.2.115:5232
# Daemon flag
#daemon = False
# File storing the PID in daemon mode
#pid =
# Max parallel connections
max_connections = 0
# Max size of request body (bytes)
max_content_length = 1000000000
# Socket timeout (seconds)
timeout = 30
# SSL flag, enable HTTPS protocol
#ssl = True
# SSL certificate path
#certificate = /etc/ssl/server_cert.pem
# SSL private key
#key = /etc/ssl/server_key.pem
# CA certificate for validating clients. This can be used to secure
# TCP traffic between Radicale and a reverse proxy
#certificate_authority = /etc/ssl/client_cert.pem
# SSL Protocol used. See python's ssl module for available values
#protocol = PROTOCOL_TLS
# Available ciphers. See python's ssl module for available ciphers
#ciphers =
# Reverse DNS to resolve client address in logs
#dns_lookup = True
# Message displayed in the client when a password is needed
#realm = Radicale - Password Required
[encoding]
# Encoding for responding requests
request = utf-8
# Encoding for storing local collections
stock = utf-8
[auth]
# Authentication method
# Value: none | htpasswd | remote_user | http_x_remote_user
type = htpasswd
# Htpasswd filename
htpasswd_filename = /etc/radicale/users
# Htpasswd encryption method
# Value: plain | sha1 | ssha | crypt | bcrypt | md5
# Only bcrypt can be considered secure.
# bcrypt and md5 require the passlib library to be installed.
htpasswd_encryption = md5
# Incorrect authentication delay (seconds)
#delay = 1
[rights]
# Rights backend
# Value: none | authenticated | owner_only | owner_write | from_file
#type = authenticated
# File for rights management from_file
#file = /etc/radicale/rights
[storage]
# Storage backend
# Value: multifilesystem
#type = multifilesystem
# Folder for storing local collections, created if not present
filesystem_folder = /mnt/disk/radicale/collections
# Lock the storage. Never start multiple instances of Radicale or edit the
# storage externally while Radicale is running if disabled.
#filesystem_locking = True
# Sync all changes to disk during requests. (This can impair performance.)
# Disabling it increases the risk of data loss, when the system crashes or
# power fails!
#filesystem_fsync = True
# Delete sync token that are older (seconds)
#max_sync_token_age = 2592000
# Close the lock file when no more clients are waiting.
# This option is not very useful in general, but on Windows files that are
# opened cannot be deleted.
#filesystem_close_lock_file = False
# Command that is run after changes to storage
# Example: ([ -d .git ] || git init) && ([ -e .gitignore ] || printf '.Radicale.cache\n.Radicale.lock\n.Radicale.tmp-*\n' > .gitignore) && git add -A && (git diff --cached --quiet || git commit -m "Changes by "%(user)s)
#hook =
[web]
# Web interface backend
# Value: none | internal
type = internal
[logging]
# Logging configuration file
# If no config is given, simple information is printed on the standard output
# For more information about the syntax of the configuration file, see:
# https://docs.python.org/3/library/logging.config.html
config = /etc/radicale/logging
# Set the default logging level to debug
#debug = False
# Store all environment variables (including those set in the shell)
#full_environment = False
# Don't include passwords in logs
#mask_passwords = True
[headers]
# Additional HTTP headers
#Access-Control-Allow-Origin = *
Si des infos sont manquantes juste me le faire savoir, je sais pas trop quoi ajouter comme infos.
Merci,
Guillaume
J'ai déployé mon serveur CalDAV avec Radicale mais je ne suis pas capable de me connecter avec mon iPhone tournant sous iOS 14.3 . Pas de problèmes avec Mozilla Thunderbird.


La seule façon dont j'ai été capable de connecter mon serveur CalDAV à mon iPhone c'est en sélectionnant Souscrire:


Comment faire pour connecter mon iPhone a mon serveur CalDAV ?
Voici mon fichier de configuration /etc/radicale/config :
# -- mode: conf --
# vim:ft=cfg
# Config file for Radicale - A simple calendar server
#
# Place it into /etc/radicale/config (global)
# or ~/.config/radicale/config (user)
#
# The current values are the default ones
[server]
# CalDAV server hostnames separated by a comma
# IPv4 syntax: address:port
# IPv6 syntax: [address]:port
# For example: 0.0.0.0:9999, [::]:9999
hosts = 192.168.2.115:5232
# Daemon flag
#daemon = False
# File storing the PID in daemon mode
#pid =
# Max parallel connections
max_connections = 0
# Max size of request body (bytes)
max_content_length = 1000000000
# Socket timeout (seconds)
timeout = 30
# SSL flag, enable HTTPS protocol
#ssl = True
# SSL certificate path
#certificate = /etc/ssl/server_cert.pem
# SSL private key
#key = /etc/ssl/server_key.pem
# CA certificate for validating clients. This can be used to secure
# TCP traffic between Radicale and a reverse proxy
#certificate_authority = /etc/ssl/client_cert.pem
# SSL Protocol used. See python's ssl module for available values
#protocol = PROTOCOL_TLS
# Available ciphers. See python's ssl module for available ciphers
#ciphers =
# Reverse DNS to resolve client address in logs
#dns_lookup = True
# Message displayed in the client when a password is needed
#realm = Radicale - Password Required
[encoding]
# Encoding for responding requests
request = utf-8
# Encoding for storing local collections
stock = utf-8
[auth]
# Authentication method
# Value: none | htpasswd | remote_user | http_x_remote_user
type = htpasswd
# Htpasswd filename
htpasswd_filename = /etc/radicale/users
# Htpasswd encryption method
# Value: plain | sha1 | ssha | crypt | bcrypt | md5
# Only bcrypt can be considered secure.
# bcrypt and md5 require the passlib library to be installed.
htpasswd_encryption = md5
# Incorrect authentication delay (seconds)
#delay = 1
[rights]
# Rights backend
# Value: none | authenticated | owner_only | owner_write | from_file
#type = authenticated
# File for rights management from_file
#file = /etc/radicale/rights
[storage]
# Storage backend
# Value: multifilesystem
#type = multifilesystem
# Folder for storing local collections, created if not present
filesystem_folder = /mnt/disk/radicale/collections
# Lock the storage. Never start multiple instances of Radicale or edit the
# storage externally while Radicale is running if disabled.
#filesystem_locking = True
# Sync all changes to disk during requests. (This can impair performance.)
# Disabling it increases the risk of data loss, when the system crashes or
# power fails!
#filesystem_fsync = True
# Delete sync token that are older (seconds)
#max_sync_token_age = 2592000
# Close the lock file when no more clients are waiting.
# This option is not very useful in general, but on Windows files that are
# opened cannot be deleted.
#filesystem_close_lock_file = False
# Command that is run after changes to storage
# Example: ([ -d .git ] || git init) && ([ -e .gitignore ] || printf '.Radicale.cache\n.Radicale.lock\n.Radicale.tmp-*\n' > .gitignore) && git add -A && (git diff --cached --quiet || git commit -m "Changes by "%(user)s)
#hook =
[web]
# Web interface backend
# Value: none | internal
type = internal
[logging]
# Logging configuration file
# If no config is given, simple information is printed on the standard output
# For more information about the syntax of the configuration file, see:
# https://docs.python.org/3/library/logging.config.html
config = /etc/radicale/logging
# Set the default logging level to debug
#debug = False
# Store all environment variables (including those set in the shell)
#full_environment = False
# Don't include passwords in logs
#mask_passwords = True
[headers]
# Additional HTTP headers
#Access-Control-Allow-Origin = *
Si des infos sont manquantes juste me le faire savoir, je sais pas trop quoi ajouter comme infos.
Merci,
Guillaume
A voir également:
- Impossible de connecter mon server CalDAV à mon iPhone iOS 14.3
- Se connecter à gmail sur téléphone - Guide
- Trousseau iphone - Guide
- Comment connecter chromecast à la télé - Guide
- Mettre une photo en widget iphone ios 18 - Guide
- Se connecter à ma boite hotmail - Guide
2 réponses

Salut,
J'avais déjà été sur ce post et sur le site en Allemand que le post propose, je suis pas très bon en Allemand mais ce que je peut comprendre c'est que la convection doit ce faire en SSL sur iOS.
Mais le problème c'est que je sais pas comment quand je cherche de la documentation, oui il en as mais elle ne semble pas claire.
Savez-vous comment faire en sorte que le serveur CalDAV prenne en charge le SSL?
Merci,
Guillaume
J'avais déjà été sur ce post et sur le site en Allemand que le post propose, je suis pas très bon en Allemand mais ce que je peut comprendre c'est que la convection doit ce faire en SSL sur iOS.
Mais le problème c'est que je sais pas comment quand je cherche de la documentation, oui il en as mais elle ne semble pas claire.
Savez-vous comment faire en sorte que le serveur CalDAV prenne en charge le SSL?
Merci,
Guillaume


